Extended ACL lab using packet tracer
In
this article we will learn about what is extended Acl , configuration of extended acl and verify the
configuration using packet tracer.
What is Extended ACL
In extended acl network admin permits or deny the network traffic using
several criteria which includes source and destination ip address,protocol and source and destination port no.This acl must be placed closest to the source. Range of extended acl is <100-199>.
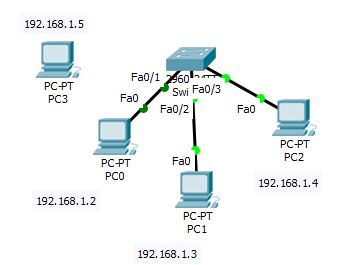
Lab Diagram
 |
| Extended ACL lab using packet tracer |
In the above diagram we have
done a simple lab setup.
Agenda of the lab are:
- · Pc0 can access the both servers.
- · Pc1 can not access both webservers.
We will do these configuration using
extended acl through packet tracer.
Configuration of Extended acl
Ip address of the inside network 192.168.1.0/24 and ip address of the outside network 172.16.0.0/24. After assign the ip address of
the devices which is located at inside and outside premises, we will configure
extended acl on router. For configuration extended acl we need to follow the below steps.
Router(config)#access-list 101 deny ip host 192.168.1.2 host 172.16.0.2
Router(config)#access-list
101 deny ip host 192.168.1.3 host 172.16.0.2
Router(config)#access-list
101 deny ip host 192.168.1.3 host 172.16.0.3
Router(config)#int
gigabitEthernet 0/0
Router(config-if)#ip access-group 101 in
Verify Configuration of Extended acl
Before doing the configuration pc1 can access both servers.
When we ping webserver1 and webserver2 from pc1we found the below output.
C:\>ping 172.16.0.2
Pinging 172.16.0.2 with 32 bytes of
data:
Request timed out.
Reply from 172.16.0.2: bytes=32
time=17ms TTL=127
Reply from 172.16.0.2: bytes=32
time=17ms TTL=127
Reply from 172.16.0.2: bytes=32
time=15ms TTL=127
Ping statistics for 172.16.0.2:
Packets: Sent = 4, Received = 3, Lost =
1 (25% loss),
Approximate round trip times in
milli-seconds:
Minimum = 15ms, Maximum = 17ms, Average
= 16ms
C:\>ping 172.16.0.3
Pinging 172.16.0.3 with 32 bytes of
data:
Request timed out.
Reply from 172.16.0.3: bytes=32
time=16ms TTL=127
Reply from 172.16.0.3: bytes=32
time=15ms TTL=127
Reply from 172.16.0.3: bytes=32
time=29ms TTL=127
Ping statistics for 172.16.0.3:
Packets: Sent = 4, Received = 3, Lost =
1 (25% loss),
Approximate round trip times in
milli-seconds:
Minimum = 15ms, Maximum = 29ms, Average
= 20ms
After the configuration of extended acl on router
when we going to communicate servers form pc1 we got the following output.
C:\>ping
172.16.0.3
Pinging
172.16.0.3 with 32 bytes of data:
Reply
from 192.168.1.1: Destination host unreachable.
Reply
from 192.168.1.1: Destination host unreachable.
Reply
from 192.168.1.1: Destination host unreachable.
Reply
from 192.168.1.1: Destination host unreachable.
Ping
statistics for 172.16.0.3:
Packets: Sent = 4, Received = 0, Lost =
4 (100% loss),
Conclusion
In this article we have learned about what is extended Acl , configuration of extended acl and verify the configuration using packet tracer.